Four Phishing Scenes Demo Manual
BadUSB Phishing CS released
Use the tool Digispark, shaped like a USB memory stick, and use the Arduino compilation to burn programs into it.
Install Arduino debugging software
- Open the Arduino website Arduino - Home and click Software.
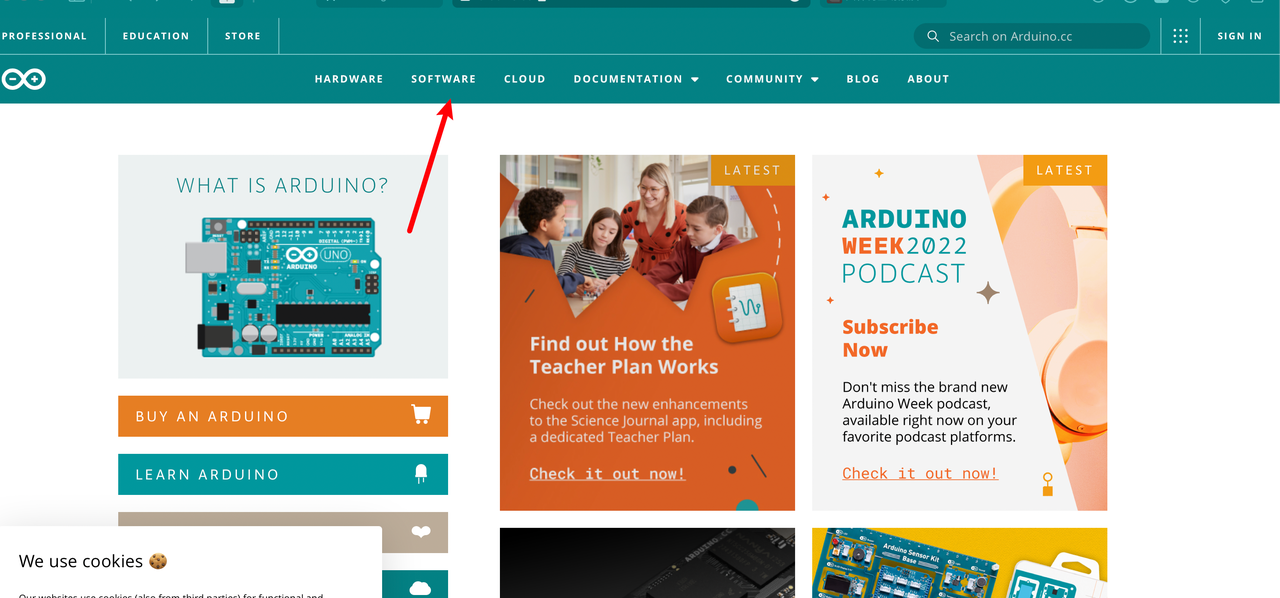
- Download the Windows version of the software (the one that says Win7 or newer on the right) to install
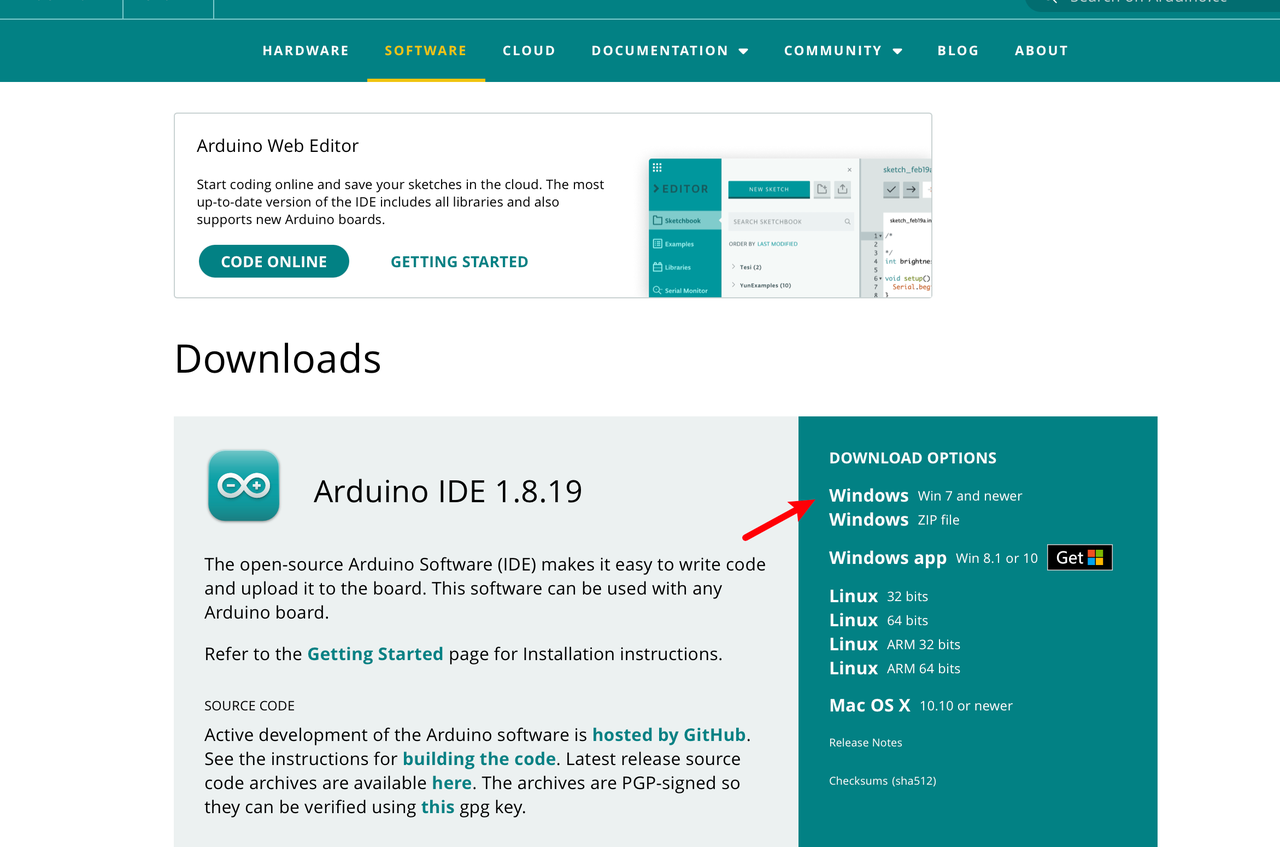
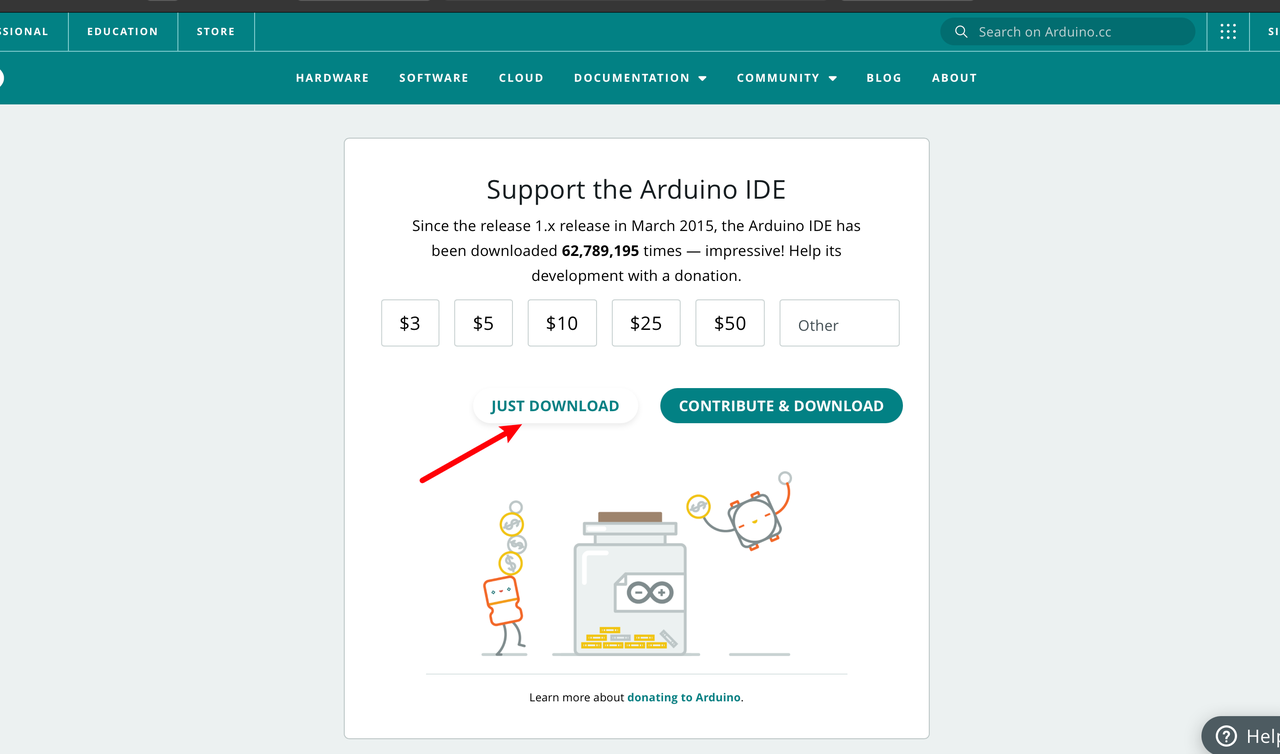
- Install the software, which will prompt you to install a USB drive, click Install
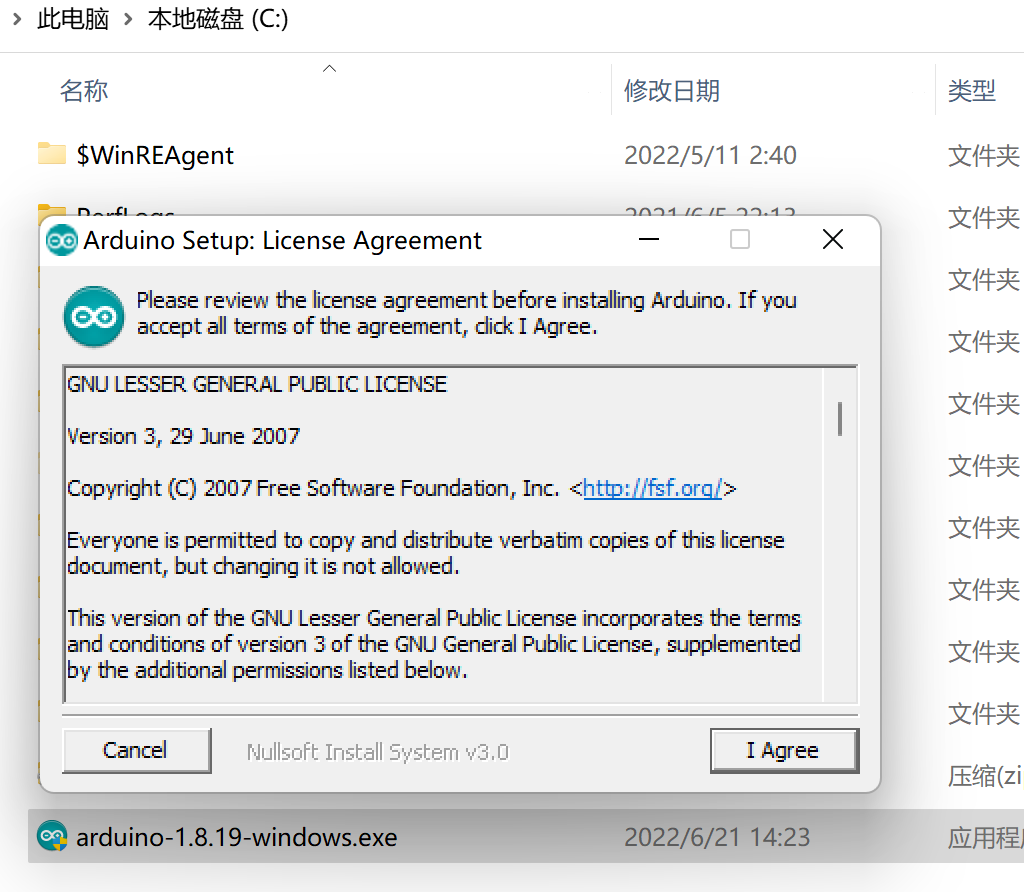
- The installation is successful as shown in the following figure
Configuring Digispark in the Arduino board
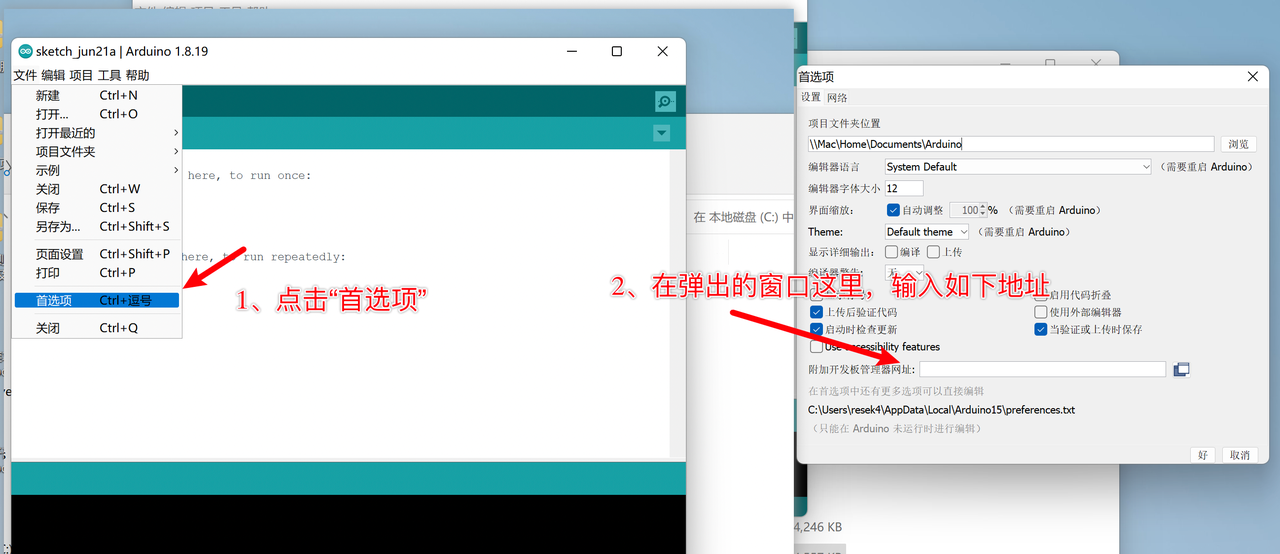
- In
Additional Board Manager URLs, add:1
https://raw.githubusercontent.com/ArminJo/DigistumpArduino/master/package_digistump_index.json
Click
Development Edition Management, and search for digistump , you can find this development version configuration information, install thisDigistump AVR Boards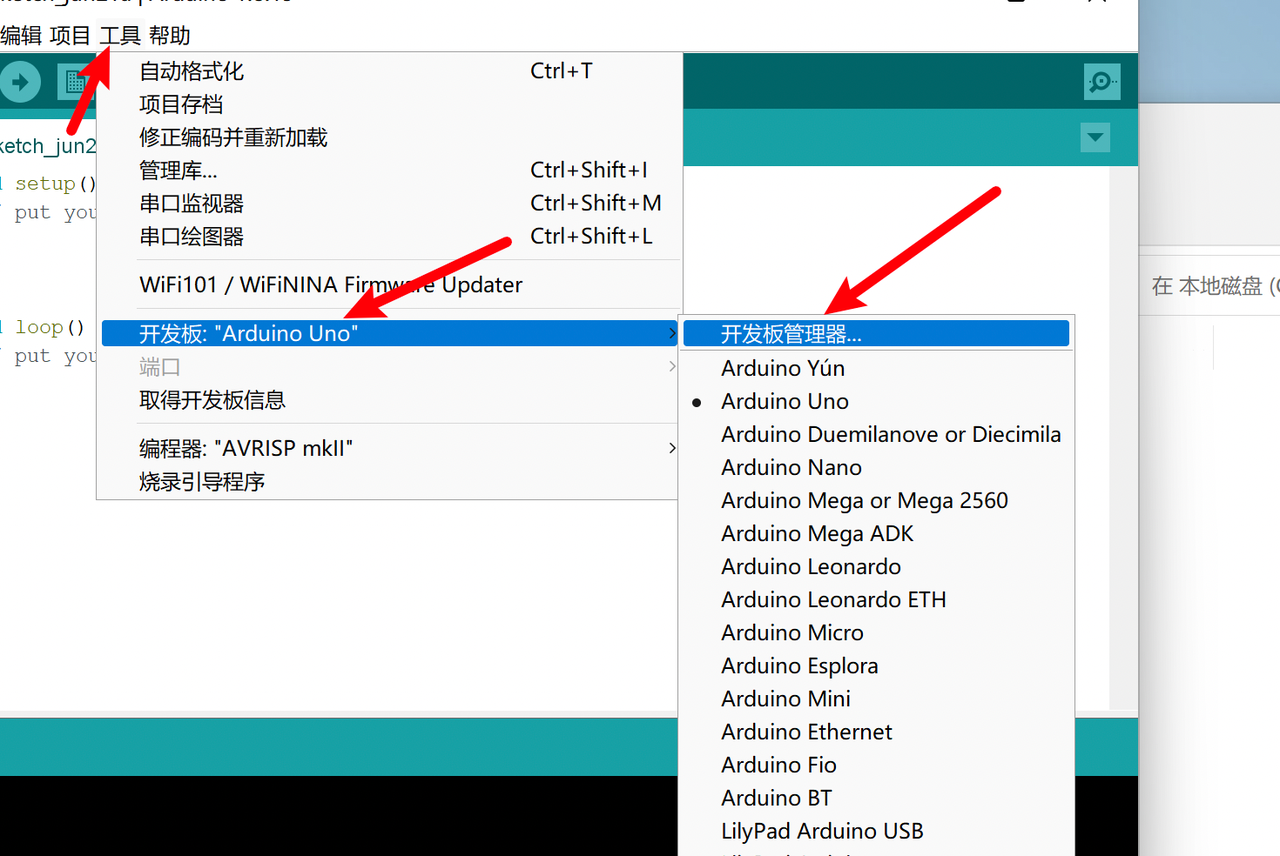
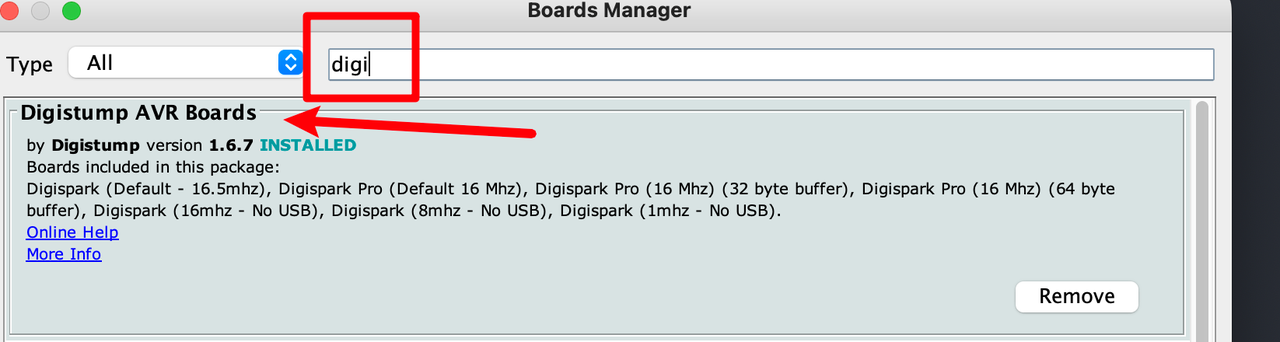
Click
Development Boards- >Digistump AVR Boards- >Digispark (Default - 16.5mhz)
Upload program
- Upload the program you want to execute, enter the code you want to upload, and click the right arrow to upload (the one on the left is verification, uploading includes the steps of verification)
When uploading, it will let you save the program in one place, save it in one place at will.
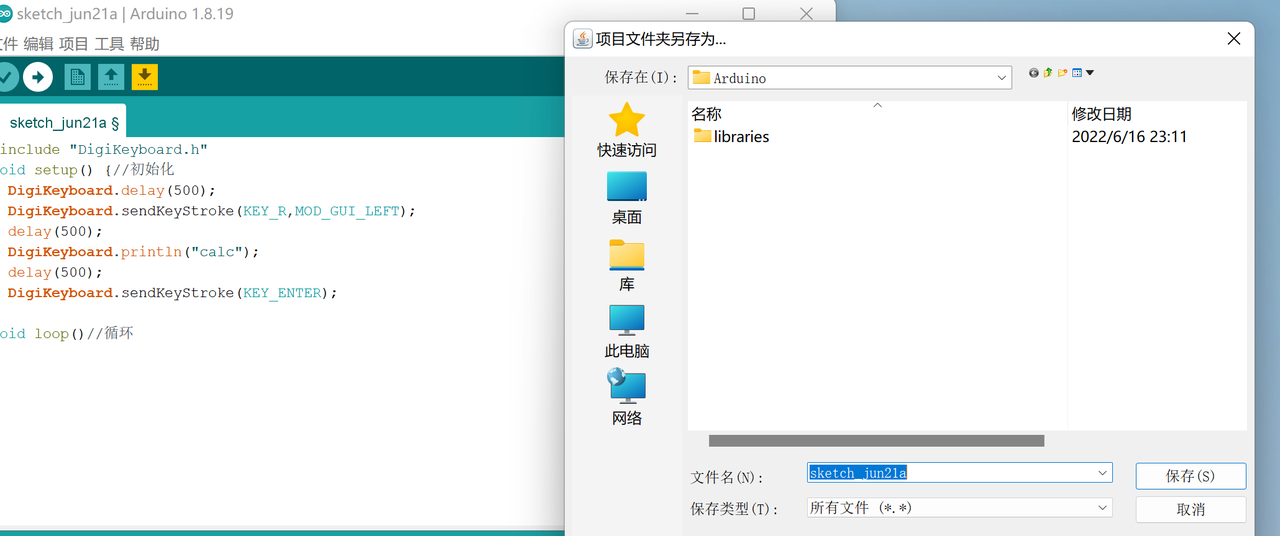
Case 1: Pop-up Notepad
If you want to pop-up notepad, burn the following program:
1 |
|
Case 2: CS release
Where xxxx is the CobaltStrike HTTP release address
1 |
|
- Insert Digispark to release it~
Mail phishing CS release
Email content
Email content (this requires the user to write a paragraph):
Recently, there has been a xx vulnerability. The company contacted the xx manufacturer to provide a xx vulnerability repair tool. Please be sure to open it for repair
Download the repair tool:xxxx
- And you can put a Trojan File into this phishing mail~
Wi-Fi Pineapple Wi-Fi Phishing information collection
Start pineapple pie, install 4 net cables and plug in power

Start the pineapple pie
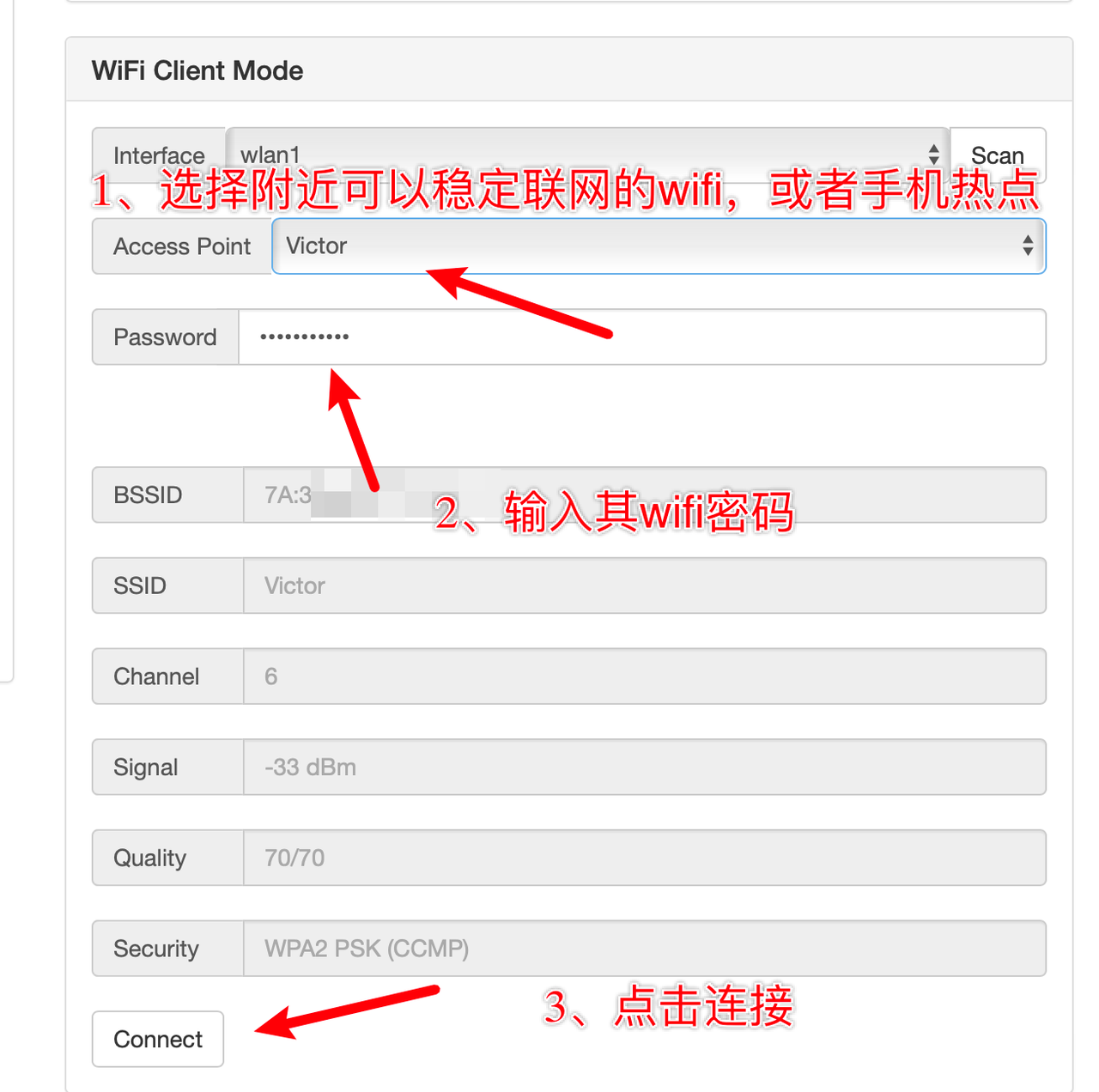
- Connect to the pineapple pie management WIFI
- Open the browser and visit the pineapple pie management address:
172.16.42.1:1471, You can access the administrative address of Wifi Pineapple
Configure network bridging (networking pineapple pie)
The purpose of this operation is to logically:
Victim -> Pineapple pie -> Internet
The network structure allows the victim to connect to the pineapple pie’s phishing wifi and still be able to access the Internet, but the victim does not know that there is a pineapple pie between him and the Internet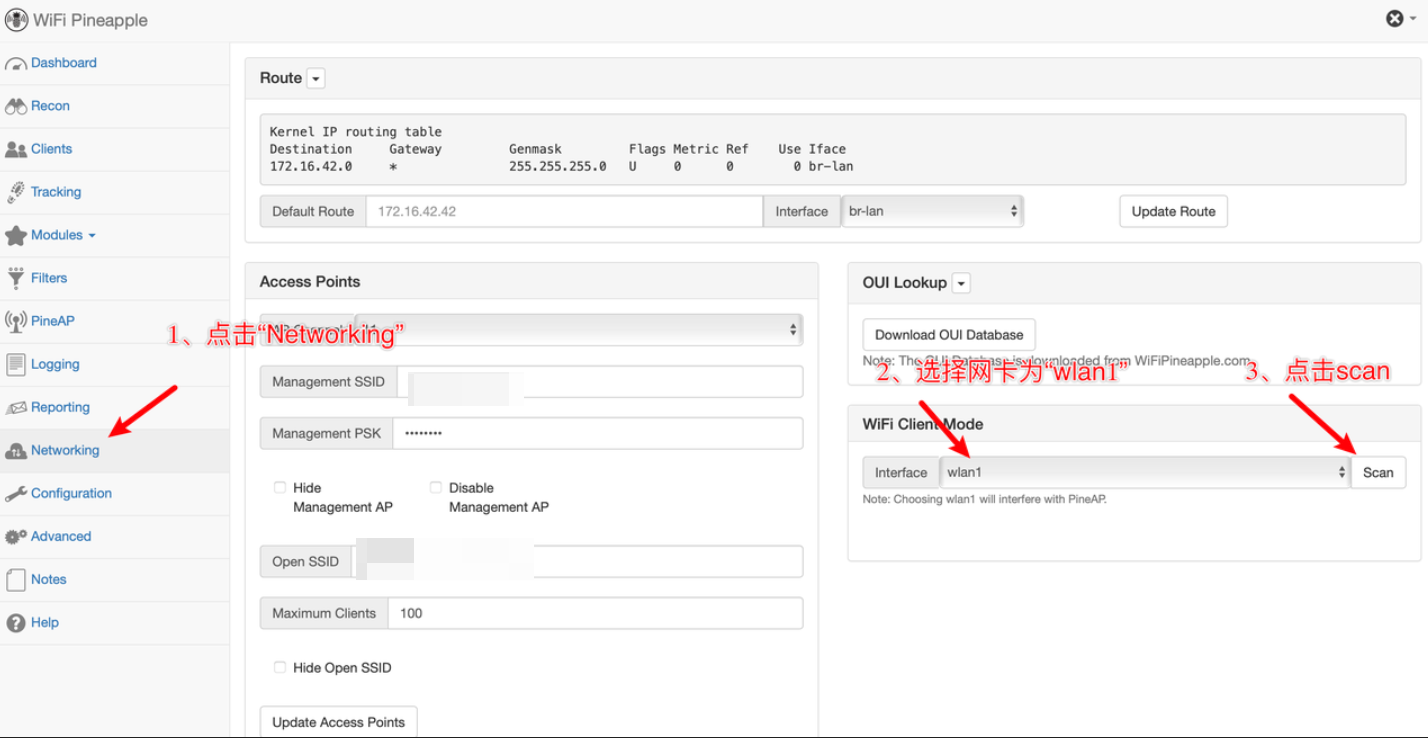
(When you click scan to scan the wifi, you can click several times until you scan the available wifi)
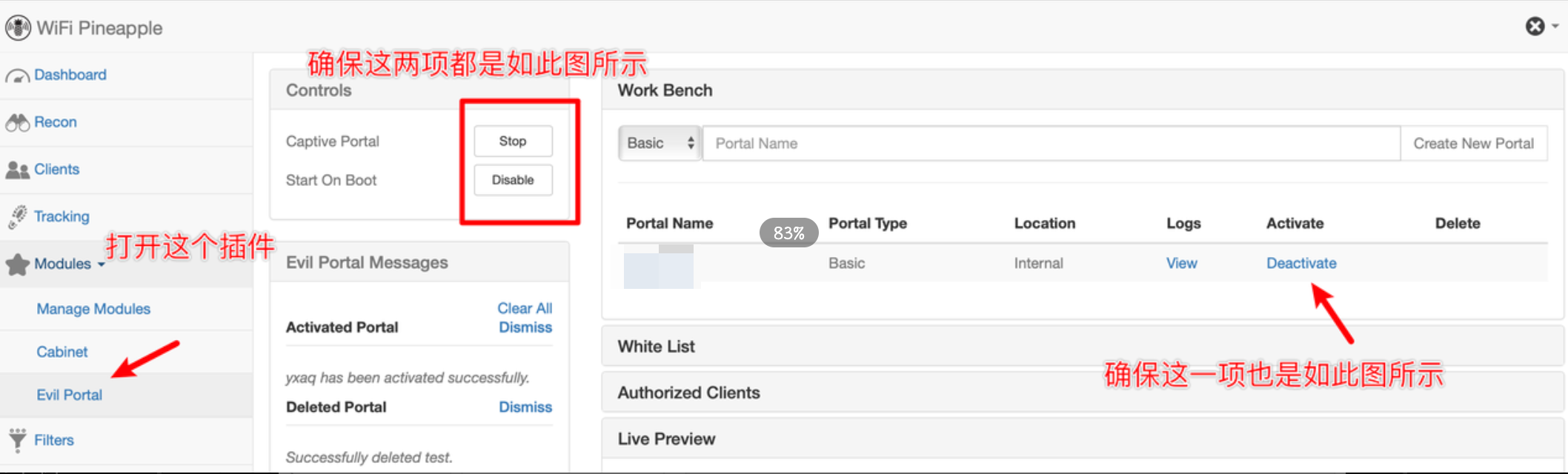
Phishing with the Evil Portal plugin
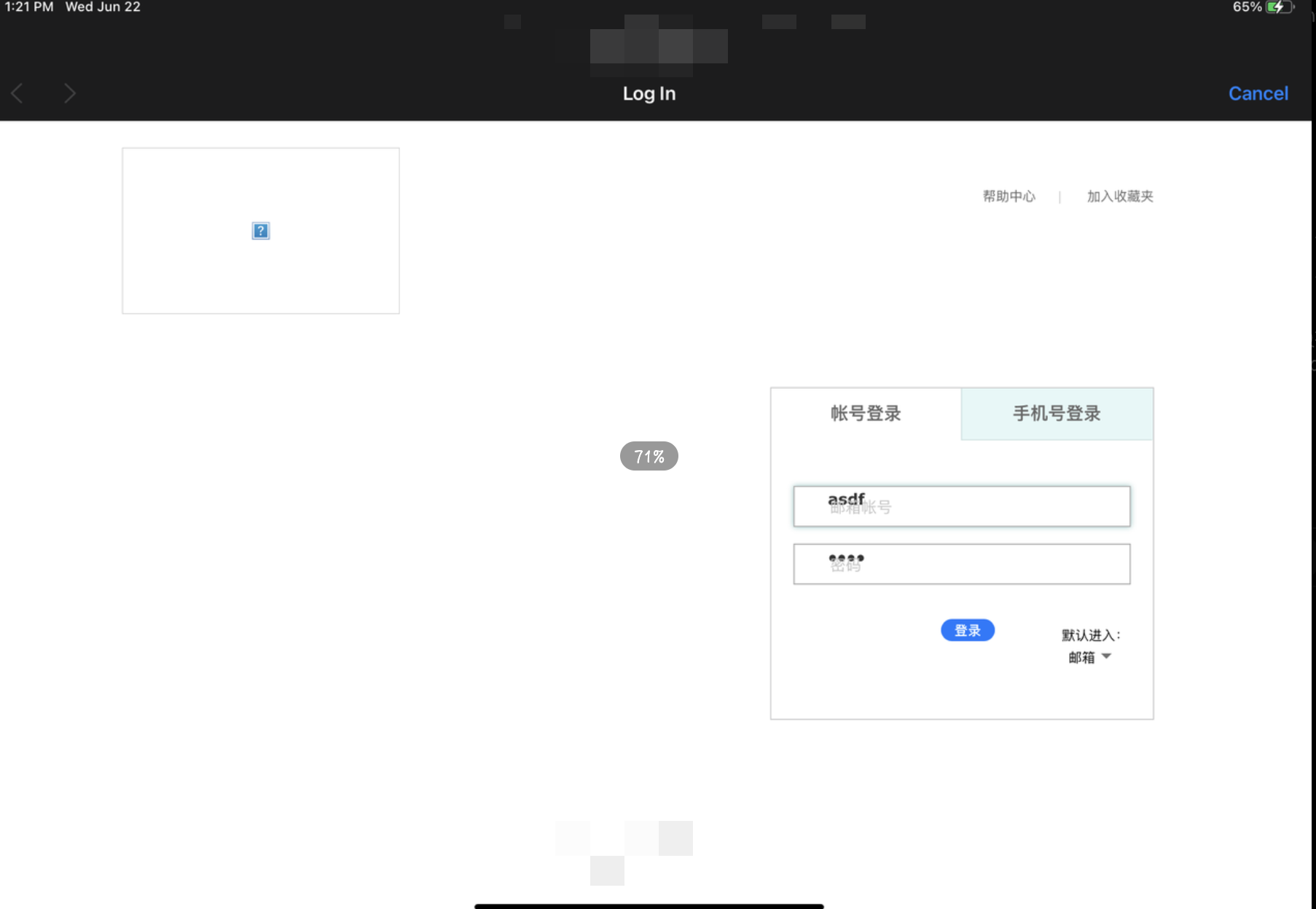
Then the victim will search for your phishing wifi SSID in his WIFI, and a pop-up window will appear on the landing page
- Enter the password and you will be phished~
If you want to make changes to the phishing page
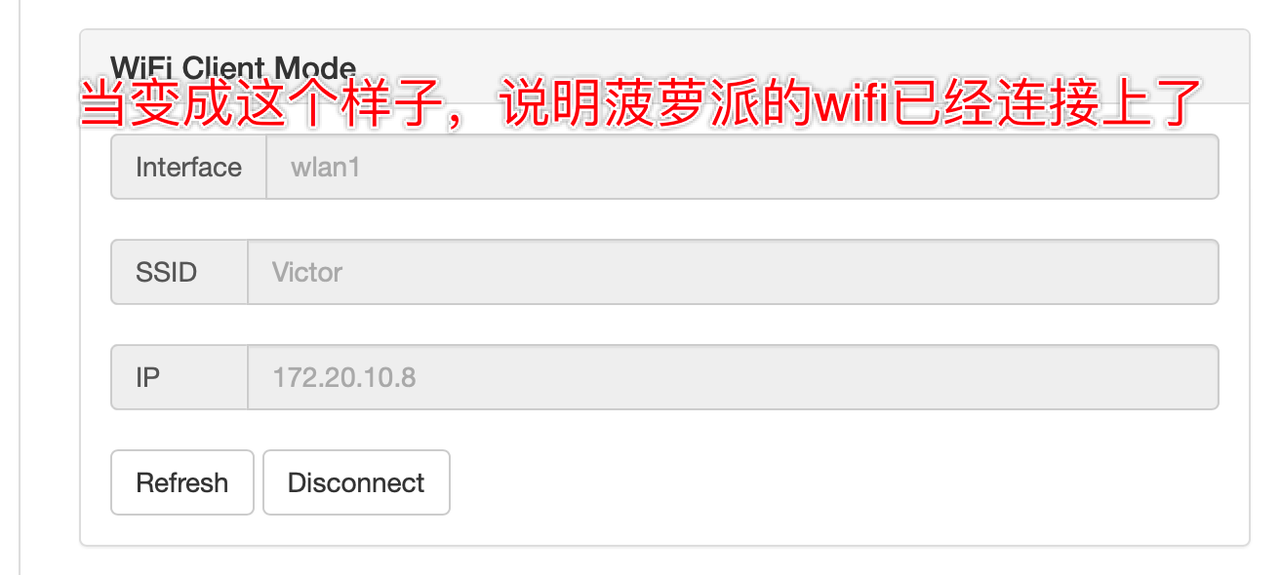
When you have bridged the pineapple pie to the network, the pineapple pie itself can connect to the external network
Connect to the pineapple pie management address just created, use XSHELL or the command line ssh connection tool, use ssh to log in to the pineapple pie terminal.
After successful login, the display looks like this.
Use the command to enter the port-xxxx directory(The filepath of your phishing website)
1 | cd portals/xxxx/ |
You can see the relevant web files, just modify them~
How to check phishing passwords
Log in to the backend of pineapple pie and enter the portal/xxxx folder
The password is stored in the pwd.txt file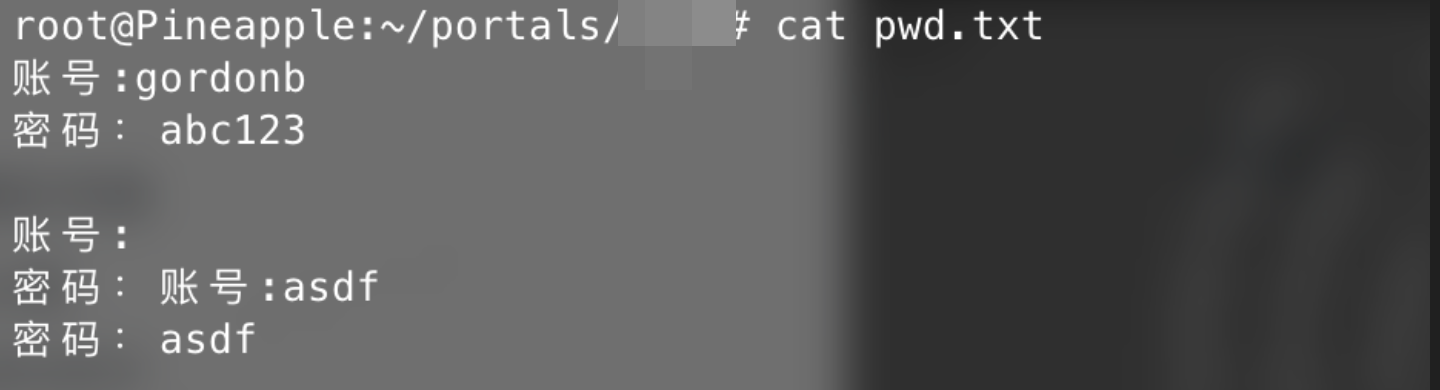
QR code phishing information collection
Let the victim directly scan the QR code, you can pop up the pop-up window of the QQ Zone (just for demonstration, modify its front-end page to make it more simulation), the victim fills in the account password, you can receive the information filled in at the server level, resulting in information leakage
Build your own QR code phishing server receiver
Visit github for a detailed build tutorial:
GitHub - Cl0udG0d/QQFishing: QQ钓鱼,社会工程
- Set up this service on your own server (you need to install docker-compose in advance), and then execute the following commands in sequence:
1 | git clone https://github.com/Cl0udG0d/QQFishing |
After setting up, access the server http://IP:5000 to access its phishing address
Generate QR code
Baidu casually search for a QR code generation online tool that can embed pictures, such as:
免费在线二维码生成器
Generate the phishing URL as a QR code, and the victim can scan the QR code to achieve the purpose of opening the phishing page, such as
(This QR code is just an example, users need to regenerate it themselves)
Four Phishing Scenes Demo Manual
https://resek4.github.io/2022/07/15/Four Phishing Scenes Demo Manual/