Learn the Blockchain

Technical terms
| Word | Description |
|---|---|
| Cryptocurrency | 加密货币 |
| Cryptographic Hash Function | 密码哈希函数 |
| (CR)Collision Resistance | 哈希碰撞 |
| Message Digest | 消息摘要 |
| Digital Commitment | 数字承诺 |
| Puzzle friendly | Bitcion的机制之一 |
| Proof of work | 工作量证明 |
| Secure Hash Algorism | SHA |
| Asymmetric encryption algorism | 非对称加密 |
| Merkle Tree | 默克尔树 |
| Merkle Proof | 默克尔证明 |
| Binary Tree | 二叉树 |
| (TX)Transaction | 交易 |
| Root Hash | 根哈希 |
| Proof of inclusion/membership | 包含证明 |
| (SPV)Simplified Payment Verification | 简化付款认证 |
| Genesis Block | 创世区块 |
| Full node | 全节点 |
| Light node | 轻节点 |
| Coinbase Transaction(Tx) | 铸币交易 |
| Distributed Consensus | 分布式共识 |
| Longest Valid Chain rule | 最长合法链原则 |
| Block Reward | 出块奖励 |
Cryptographic Hash Function
2 Features: Collision Resistance
$$A \neq\ B$$$$H(A) = H(B)$$
To avoid this situation, expanding the Value space is necessary.
One solution is appending a random number After the message A, and calculating the Hash result.
This feature can’t be proven by math.
Collision Resistance can make a message be a Message Digest, to detect the Tamper happening.
2 Features: Hiding
- Irreversibility: You can not get the A value if you only know the H(A) itself.
- The effect of Digital Sealed Envelop: Because of the hiding feature, Your message can do the forecasting stuff.
The principle of Blockchain’s mining
To prevent the input space too small to cause the Collision Resistance problem, each block message should add a random nouce number after itself.
The miner should use the hash algorithm to calculate this random nonce number, and if the Hash result approach this situation.
$$H(A+nonce) \leq\ Target$$
This block can be put on the blockchain, And the calculation can be looked at as the Proof of Work
- Also, The design model of blockchain should be difficult to solve, but easy to verify
Asymmetric Encryption Algorithm
Encryption process: A uses B’s public key to encode the message, and B uses its private key to decode it.
Signature process: A uses its private key to encode the message, and B uses A’s public key to decode it.
The Signature process was used when encapsulating a transaction(Tx) block, to prove the initiator of the transaction.
The process of “encryption” was used when describing the number of transactions, to prove the actual transaction amount
- The public or private key should use a great random source to ensure its randomness.
Data structure
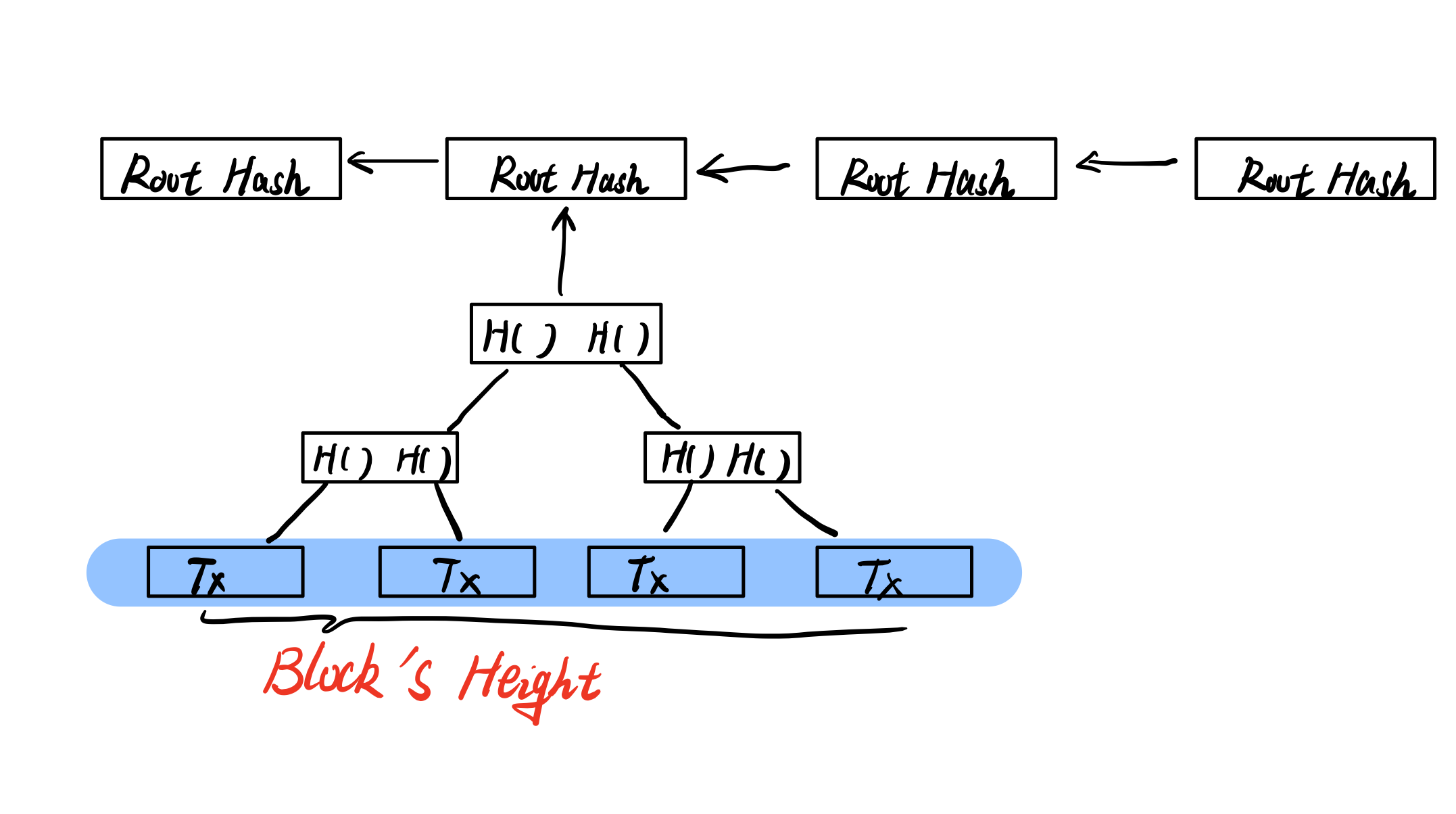
- Blockchain is a linked list using a hash pointer.
- Blockchain uses the Merkle tree to create itself.
There are two kinds of nodes to save the transaction information.
Full node: Include both the Block header and the Block body.
Light node: Only include the Block header(according to the SPV), like the mobile application.
Every transaction should base on a theory: Who transacting, who proving
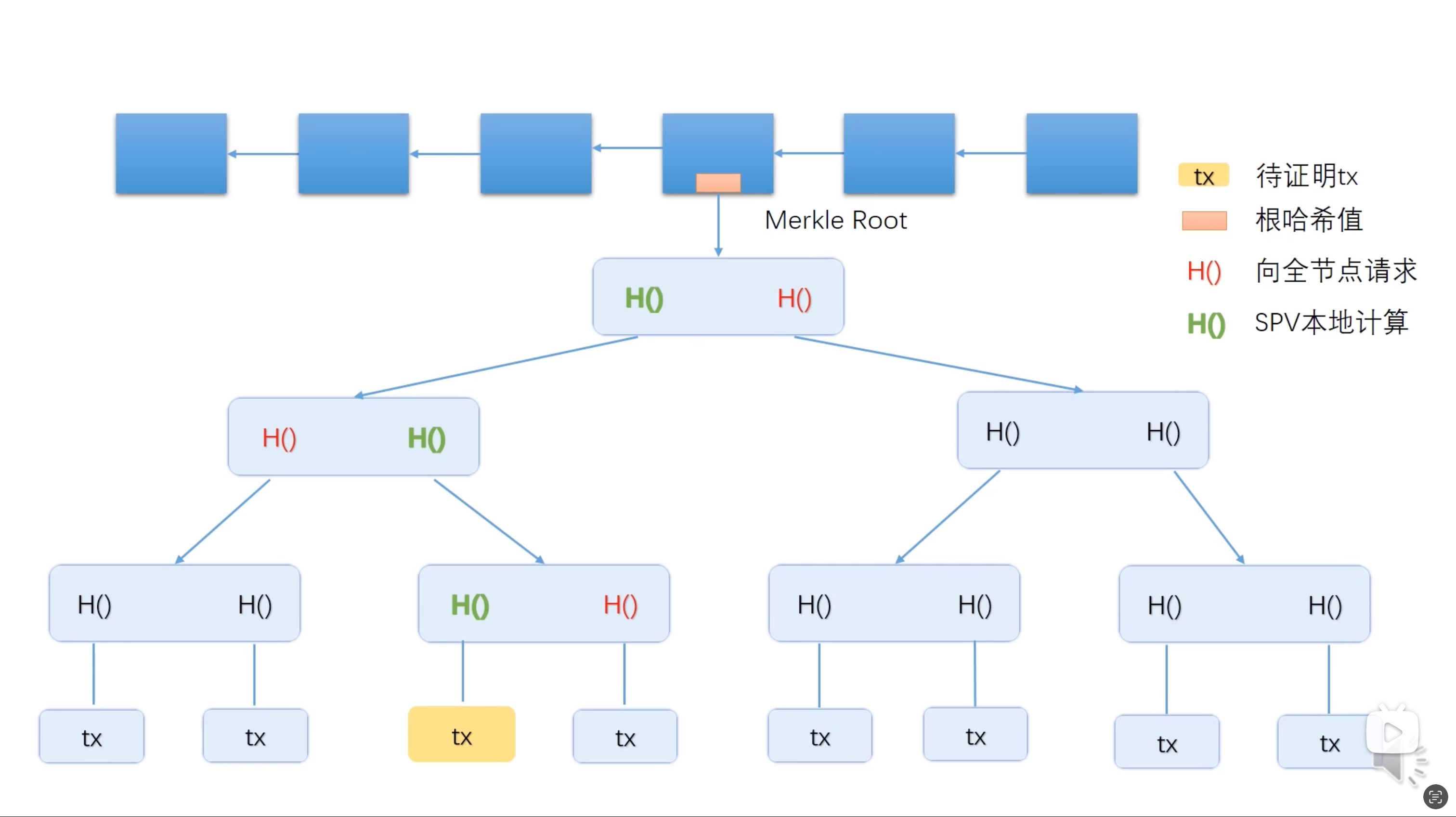
When a light node wants to prove a transaction(Tx) is real, it should:
- Send a request to the full node, contains with the Tx’s hash.
- The full node uses the Tx’s hash to search the entire Merkle tree’s branch and provides the Red H() to the light node.
- The light node uses the Red H() and combines the currently Tx’s Hash(Green H()) to verify the hash of the block, until to the Root hash.
- If the verify completely right, then the transaction can be proved right either.
When a light node wants to prove a transaction(Tx) is not real, it should:
- Send a request to the full node, contains with the Tx’s hash.
- The full node sorts all the blocks based on their hash values and returns Tx’s before and after blocks hash to the light node.
- The light node calculates the Block Hash which combines the before and after block until to the root hash, if the root hash is the same as the current one, then this transaction is unreal(Because this transaction never exists, so the hash wasn’t changed).On the contrary, if the transaction truly existed, the result of the block hash around the Tx, mustn’t be the current one.
Protocol
Basic Theory
Any type of token should have two sides features:
- Authentication of the token’s issuer
To ensure the token’s reality - Transaction Log(Release Code, Transaction information, etc…)
To ensure the token was created by the issuer, not the copying.
Each transaction has two ‘inputs’ and 1 ‘outputs’:
- Inputs: Coin’s source and Sender’s public key
- Outputs: Receiver’s public key
The coin’s source ensures this transaction’s reality.
The sender’s public key ensures the sender is not fake. (But attention, this public key comes from the Coinbase Block, not the sender itself)
The receiver’s public key enlights this transaction’s hash pointer. (transfer to whom).
A block always encapsulates many transactions(Tx), all of these transactions combine into a block as a Merkle tree, and the quantity of these transactions is called the block’s height.
A full node block has two parts of it: Block header, Block body
The Block header was made up of these below things:
- Blockchain version
- Hash of the previous block header. (Hash pointer)
- Merkle tree hash
- target(nBits)
- nonce
Consensus
A main feature of blockchain is [[Distributed Consensus]]
In the Bitcoin system, if it wants to reach the distributed consensus, the system must consider the membership of all nodes.
It can not make any decisions by the number of accounts, cause it may lead to the [[Sybil Attack]].
So, using the Calculating power(By letting the miner calculate the nouce, “solve the problem”) to measure the membership is a better way to reach consensus.
Longest Valid Chain Rule
The blockchain tends to let the longest chain be the main chain.
If this situation happens(like the image below): A transfers $5 to B, then A transfers the same money to the fake A(A’), it may lead to the [[Forking Attack]], but if there is another transaction after the A to B Tx, according to the longest chain rule, the attack couldn’t happen.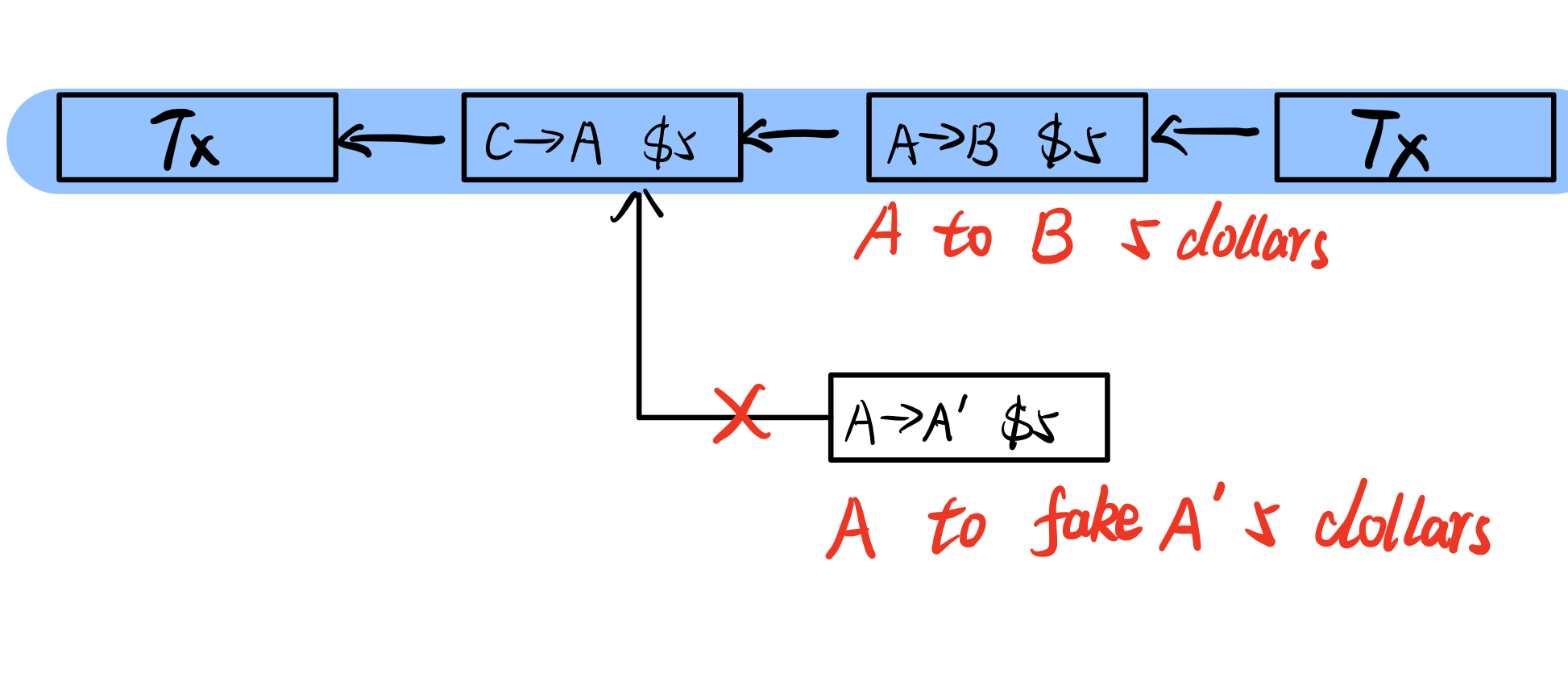
However, If two valid blocks make the chain forked, then the blockchain would choose the smaller delay one as the main chain.
And the other block will be orphaned, called the Orphan block.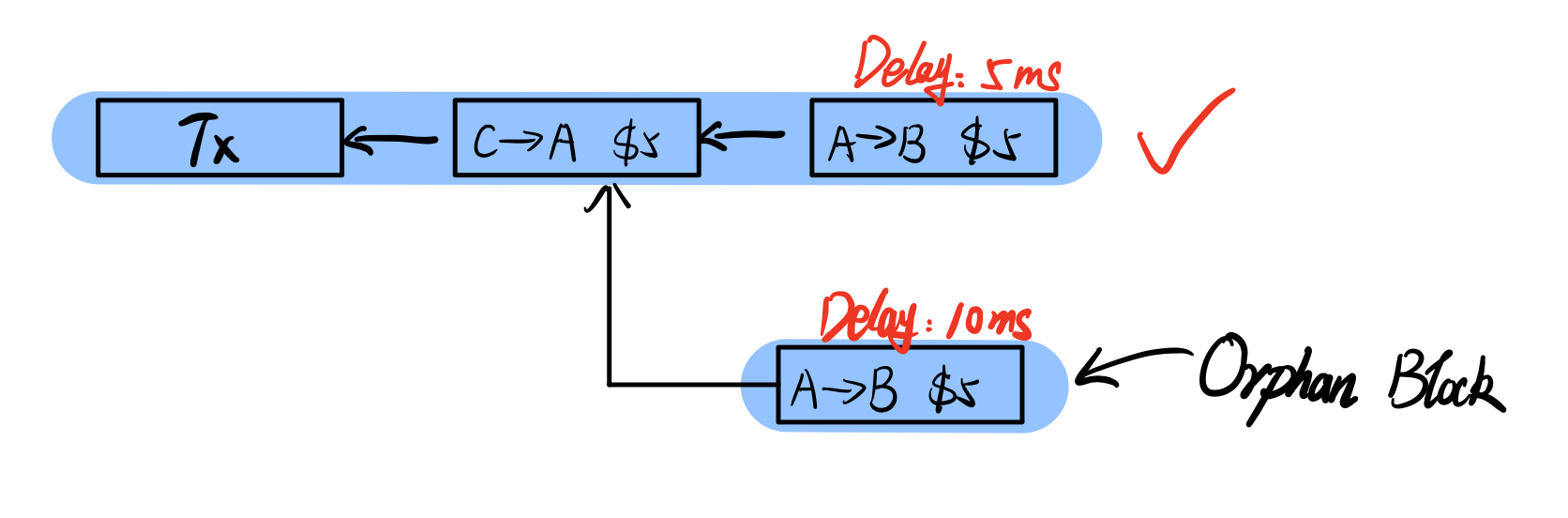
- [[Selfish Mining]] is also follow the Longest Valid Chain Rule.
Achieve
This is a piece of classic block information:
UTXO
- A full node also can do the [[UTXO]](Unspent Transaction Output) stuff.
Mining Theory
- The Bitcoin system is always waiting for 6 confirmations to confirm a transaction(6 transactions before) is irrevocable.
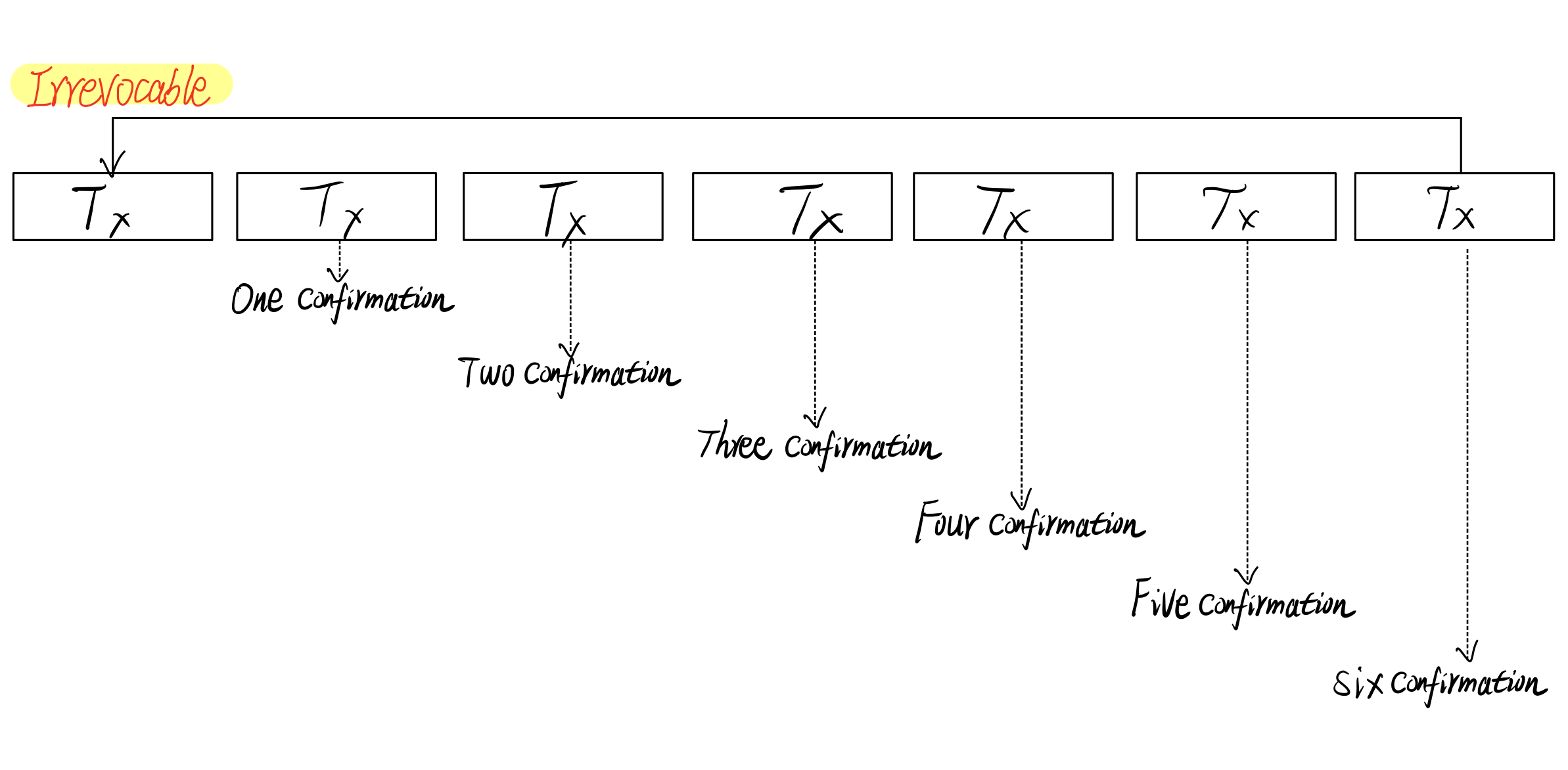
Miner will get the reward by mining(package the block, solve the difficulty), the reward contains two parts:
Block Reward
- Bitcoin is secured by mining, mining is better than voting by the membership.
The Bitcoin system regulates that Every 21000 blocks the block rewards be decreased by half.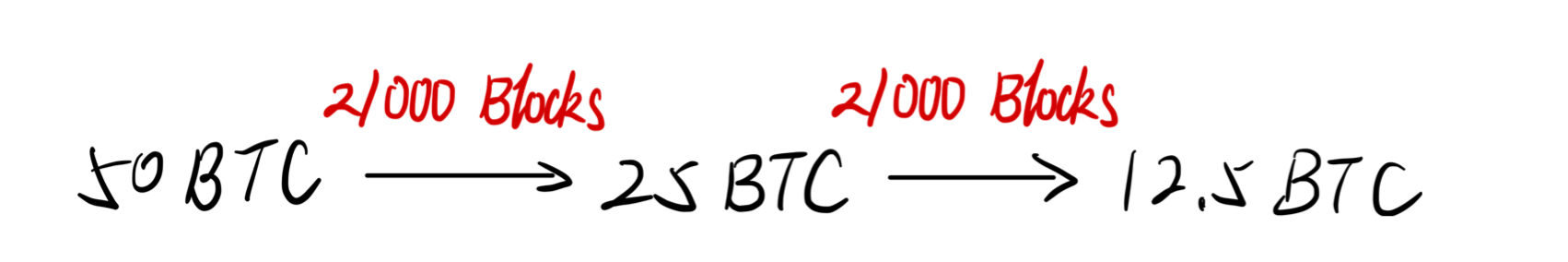
On average, the Bitcoin system will create a block per 10 minutes, which means 21000 blocks will cost 4 years, which means every 4 years the Block Reward will be decreased by half.
Although the Block Reward is decreasing, the value of Bitcoin itself increasing year by year. So the motivation for mining is also sufficient.
The Bitcoin system always adjusts the target difficulty to make the average Block time to be 10 minutes every block.
Gradually, the trend will become a Geometric Series, and the total BTC is stable: 21000000 BTC
It means that there is half of BTC at least has been mined in past.
Transaction Fee
Each transaction always satisfies this relation:
$$Total\ Inputs \geq Total\ Outputs$$
For example, if A wants to transfer 1 BTC to B and B can only receive 0.99 BTC, The 0.1 BTC is the Transaction Fee to pay for the miner.
Mining Distribution
- Every mining action can seem like a [[Bernoulli Trail]], these Bernoulli Trail constitute the Bernoulli Process(A sequence of independent Bernoulli trials)
The Bernoulli Trail’s memoryless feature guarantees the blockchain’s fairness, imagine that a node has the 10 times calculating power of another one, if the system is memorable, the advantage of the high power node will expand unlimitedly, then the weak one has no chance to defeat it ever. - Because mining blocks is a low probably process, all the mining actions can seem like a [[Poisson Distribution]].
- From a global perspective, every block time of a blockchain is an [[Exponential Distribution]].
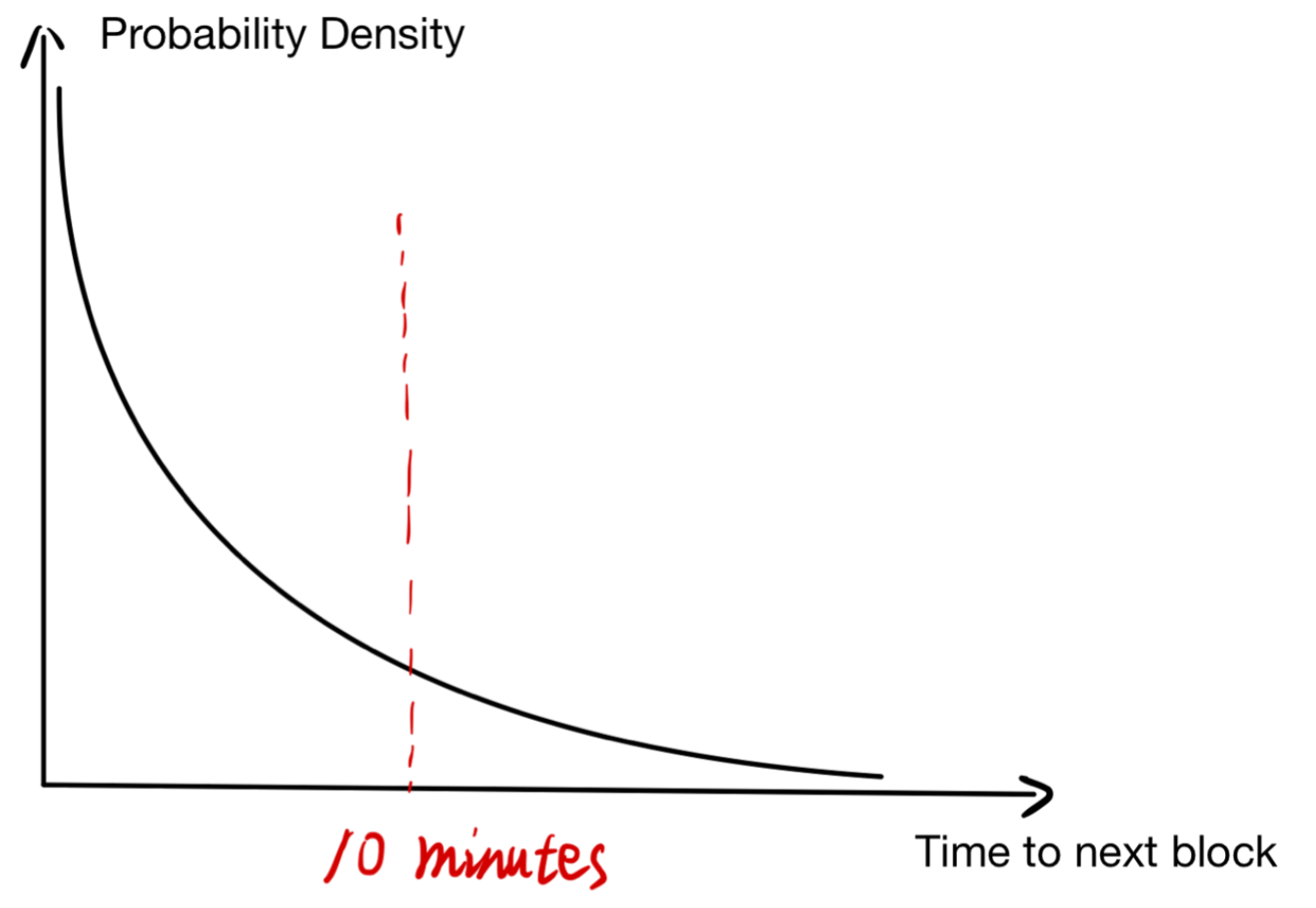
- If the past behavior will not affect to the future’s, it called Progress Free
Guarantee the Blockchain difficulty demand
Because these years, too many miners mining the block to guarantee the Blockchain difficulty demand, causing the nonce is a 32bits non-symbolic integer, so we could adjust the Merkle root hash and time(cause the transaction no need to record a specific time) to increase the difficulty.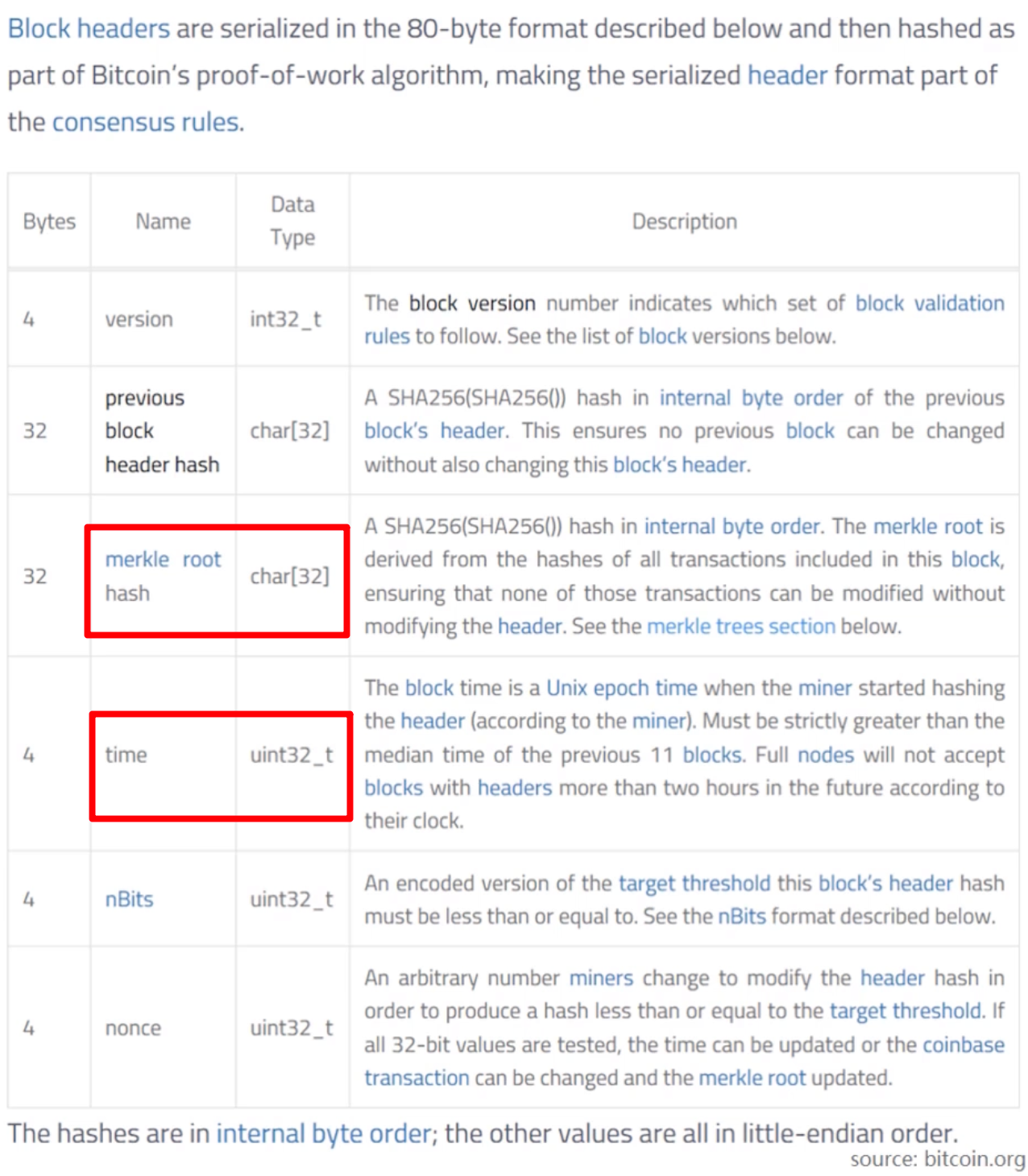
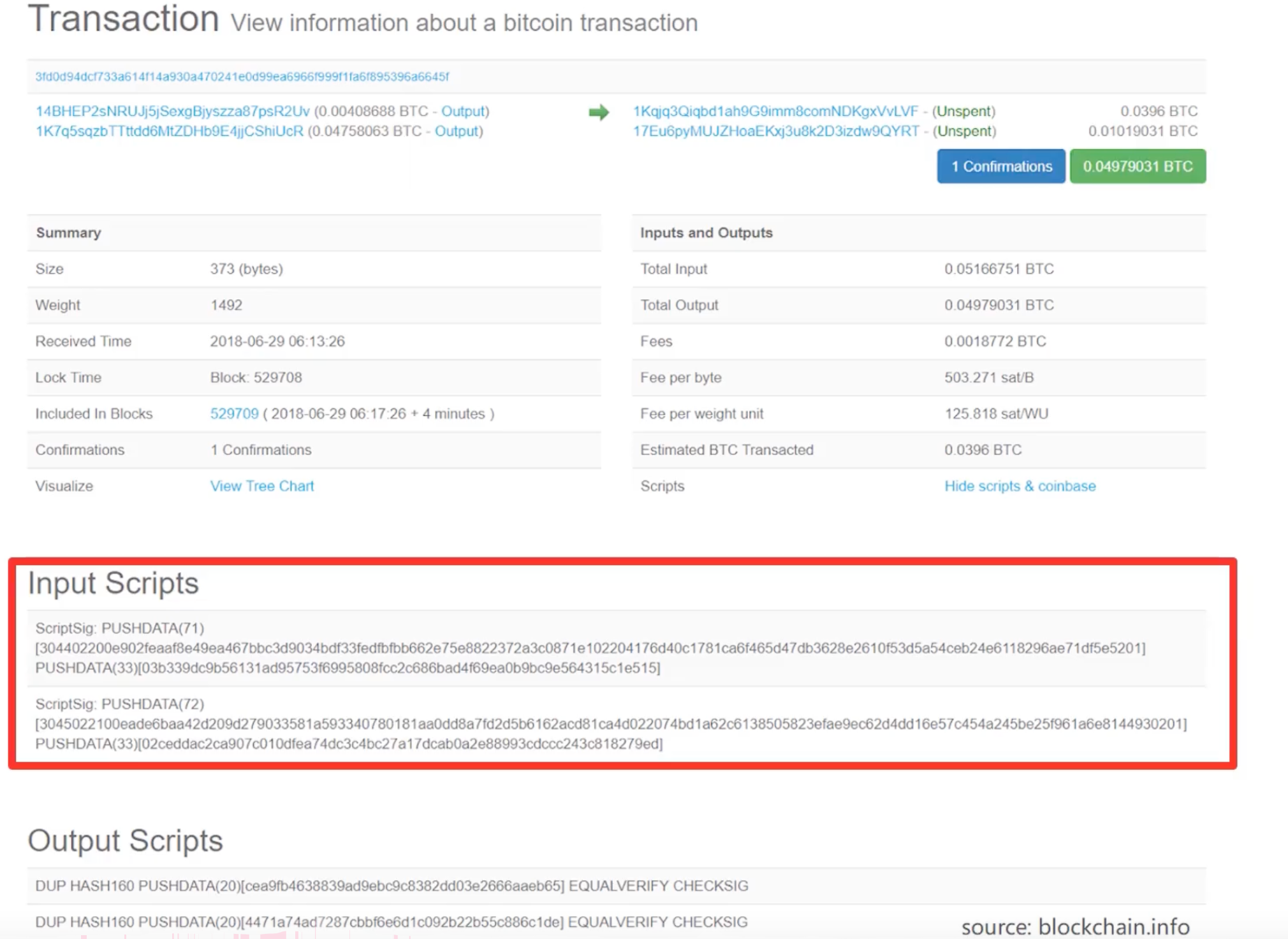
Legality of transaction
Every transaction has Input scripts and Output scripts. When the previous transaction’s Output Scripts stitch with the current transaction’s Input Scripts, and the scripts successfully run, which means the current transaction is legal.
Network
The Bitcoin system is based on the application layer in the network, and it uses P2P(Peer to Peer) Overlay Network in its network layer.
Bitcoin’s network is simple, and robust, but not efficient.
When a node receives a message, it will “flood” to other neighbor nodes. (The neighbor is a logical concept, not a real geographic neighbor)
The Bitcoin network follows the Best-effect Delivery standard.
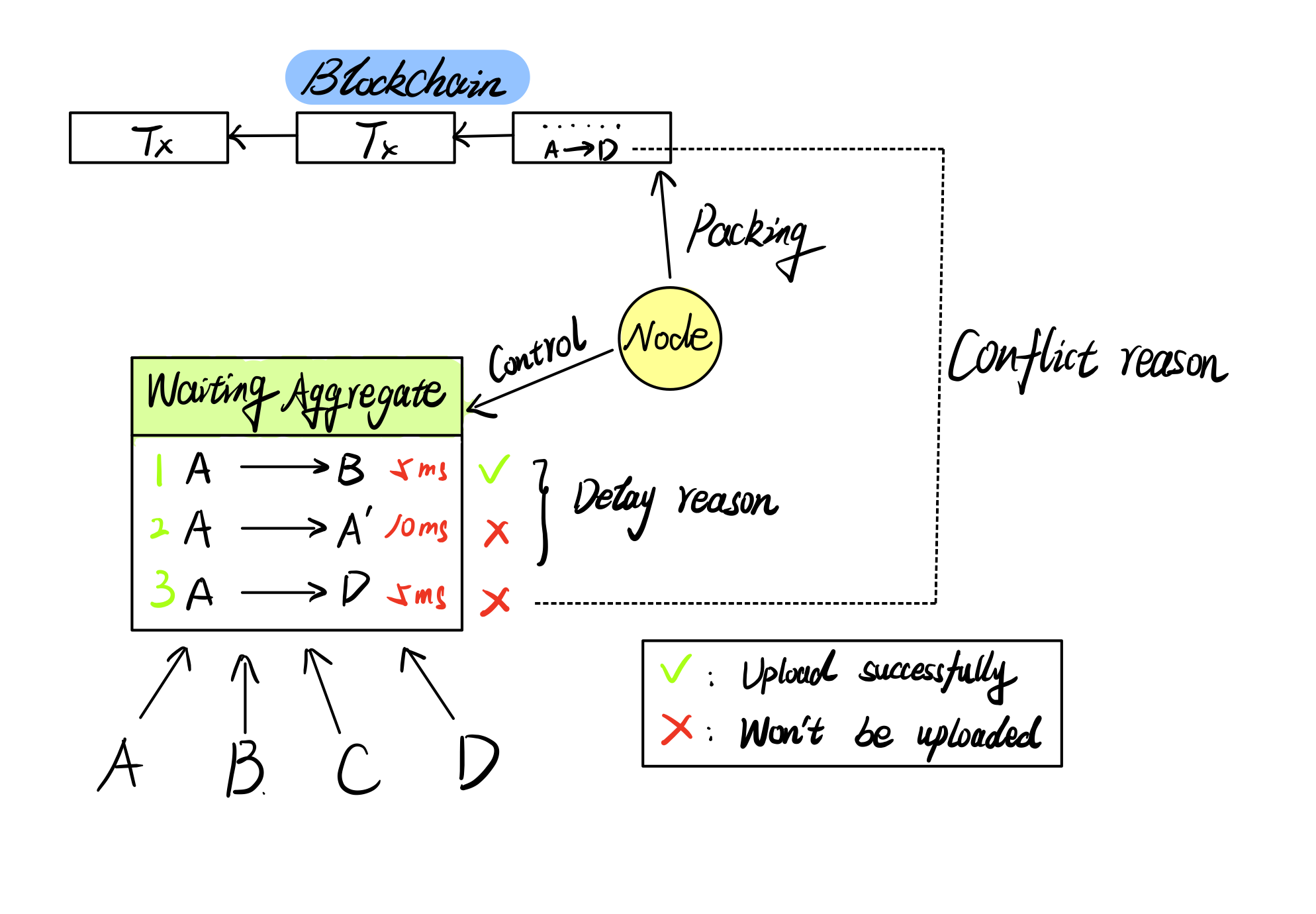
When a transaction wants to get into Blockchain, it will be joined into an aggregate by a node.
Learn the Blockchain